Docker Engine
Website Visitors:Docker Engine is a containerization platform that allows you to run applications in isolated environments, called containers, on a host operating system. It provides a lightweight and portable way to deploy applications, ensuring consistency and reliability across different environments. In short, docker engine is the host with docker installed on it.
Docker Engine consists of several components:
-
Docker Daemon:
- Description: The core service for running containers.
- Function: It listens for Docker API requests and manages Docker objects such as images, containers, networks, and volumes.
- Role: Handles the heavy lifting of building, running, and managing Docker containers.
-
Docker CLI:
- Description: The command-line interface used to interact with the Docker Daemon.
- Function: Provides commands for managing containers, images, networks, and more.
- Role: Acts as the primary user interface for developers and system administrators to interact with Docker.
- You can install cli only, on a separate machine and connect to the docker daemon/API and interact with it. Using
-Hparameter you can connect to a remote docker host. Ex:docker -H=remote-docker-engine:2375 run ImageName
docker -H=10.10.1.10:2375 run nginx
-
Docker API:
- Description: A REST API that provides programmatic access to Docker Daemon functions.
- Function: Allows other tools and applications to interact with Docker Daemon, enabling automation and integration with other systems.
- Role: Facilitates remote and programmatic control over Docker operations.
Docker Engine provides several benefits, including:
- Isolation: Containers run independently, without interfering with each other or the host system.
- Portability: Containers are portable across environments, ensuring consistency and reliability.
- Lightweight: Containers are much lighter than virtual machines, requiring fewer resources.
- Efficient: Containers share the host’s kernel, reducing overhead and improving performance.
Docker Engine is widely used in development, testing, and production environments, and is a popular choice for deploying microservices, web applications, and other distributed systems.
Namespace
In Docker, namespaces are a fundamental Linux kernel feature that Docker leverages to provide isolation for containers. Namespaces are used to ensure that a container’s processes, file systems, network, and other resources are isolated from those of other containers and the host system. Here are the key types of namespaces Docker uses:
-
PID Namespace:
- Isolates the process IDs (PIDs) of containers from each other and the host.
- Each container has its own PID namespace, meaning processes in one container cannot see or interact with processes in another container or the host.
-
Network Namespace:
- Provides each container with its own network stack, including its own IP addresses, network interfaces, routing tables, and so on.
- Containers can have isolated or shared network namespaces, allowing flexible networking configurations.
-
Mount Namespace:
- Isolates the file system mount points.
- Each container has its own mount namespace, meaning it can have its own view of the file system, including its own root file system and mounted volumes.
-
IPC Namespace:
- Isolates inter-process communication (IPC) mechanisms such as shared memory, semaphores, and message queues.
- Ensures that IPC resources used within a container are not accessible to processes outside the container.
-
UTS Namespace:
- Isolates the system identifier and hostname.
- Allows a container to have its own hostname and domain name, different from the host system.
-
User Namespace:
- Maps user and group IDs inside a container to different IDs on the host.
- Enhances security by allowing containers to run as non-root users while still appearing to have root privileges within the container.
By using these namespaces, Docker ensures that each container operates in a separate and isolated environment, enhancing security and reliability. This isolation is a key feature that allows Docker to provide lightweight and portable containerized applications.
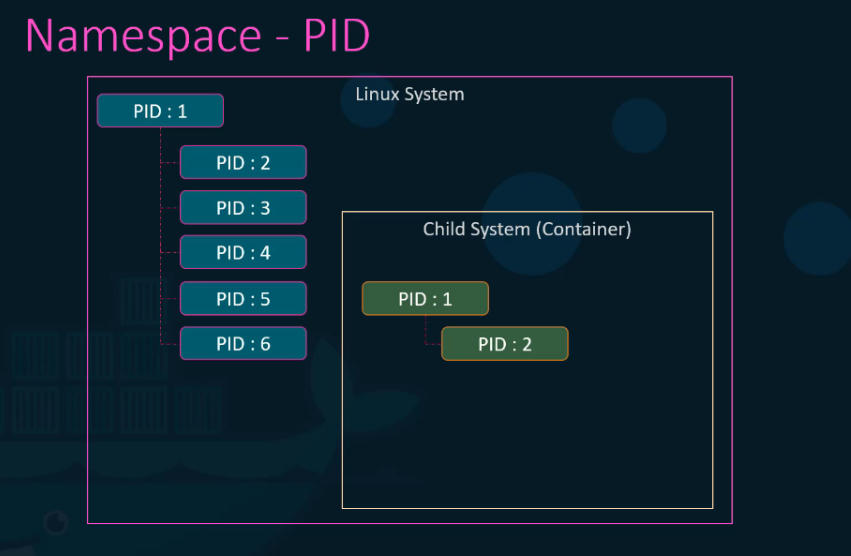
PID Namespace Explained
The PID namespace is one of the key namespaces used by Docker to provide process isolation for containers. Here’s a brief overview:
PID Namespace
- Isolation of Process IDs: The PID namespace ensures that processes within a container have their own unique process ID (PID) space. This means that a process in one container can have the same PID as a process in another container, without any conflict.
- Independent Process Tree: Each container has its own independent process tree. Processes within a container can only see and interact with other processes within the same PID namespace. They cannot see processes in other containers or on the host system.
- Security and Management: By isolating the process IDs, the PID namespace enhances security and simplifies process management. Processes in a container run in an isolated environment, reducing the risk of interference or attacks from other containers or the host.
- Parent-Child Relationship: The host system can still have visibility over all containers and their processes, often represented as a parent namespace to all container PID namespaces. This allows system administrators to manage and monitor container processes from the host.
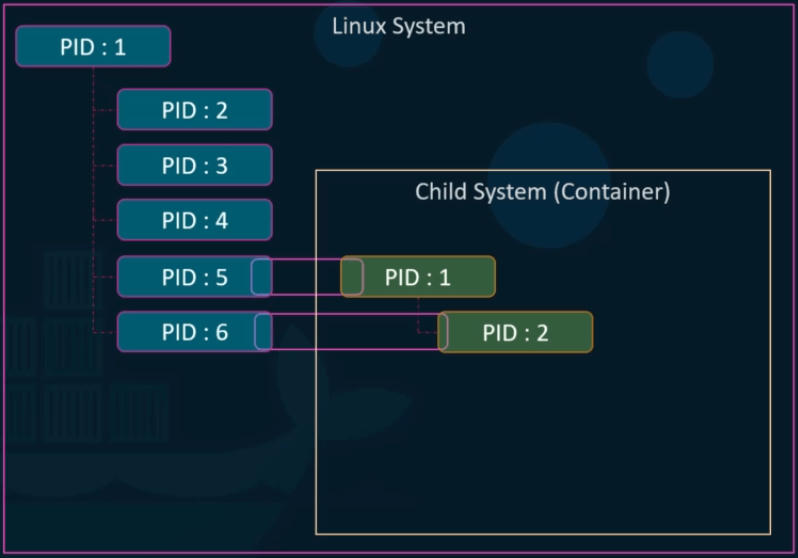
As shown below, the host machine has its own PID1, and 2 and so on.. container also has its own PID1, and 2 and so on.. but the child container maps its processes to the host.
Example Scenario
- Host System: The host might have processes with PIDs 1, 2, 3, etc.
- Container 1: When a new container is created, it has its own PID namespace starting from 1. So, the first process inside this container might have PID 1 (e.g., init or some service).
- Container 2: Similarly, another container will start its PID numbering from 1 independently of Container 1.
Benefits
- Process Isolation: Enhances security by ensuring that processes in one container cannot interfere with processes in another container or the host.
- Namespace Hierarchy: Provides a clear hierarchical structure for managing processes within containers while still allowing the host system to oversee all processes.
By leveraging PID namespaces, Docker provides strong isolation for containerized applications, which is crucial for running multiple containers on the same host without conflicts or security issues.
Restrict CPU and Memory usage in Docker Containers
To restrict a Docker container to use only 50% of the CPU or 100 MB of memory, you can use the --cpus and --memory options when running the docker run command.
Using --cpus and --memory Options
|
|
--cpus="0.5": Limits the container to use only 50% of the CPU.--memory="100m": Limits the container to use a maximum of 100 MB of memory.- In the command you can use only
--cpusoption to restrict CPU or--memoryoption to restrict memory usage. You don’t have to use both the parameters as compulsory.
Example
|
|
This command will start an nginx container that is restricted to using 50% of the CPU and a maximum of 100 MB of memory.
By using these options, you can effectively control the CPU and memory resources allocated to a Docker container.
Your inbox needs more DevOps articles.
Subscribe to get our latest content by email.